CJIS Vendor Compliance Program
Overview
The CJIS Vendor Compliance program addresses the requirement that state and national fingerprint-based background checks are completed for vendor personnel who are involved with the administration of criminal justice and have unescorted physical or virtual access to criminal justice information (CJI) within the state of Georgia. Entities that would benefit from this program include vendor personnel involved with the maintenance of computer systems, shredding companies and live scan vendors. The CJIS Vendor Compliance program reduces the need to run duplicate background checks for the same vendor personnel therefore making it easier for vendors that contract with Georgia criminal justice agencies to meet FBI CJIS Security Policy (CSP) personnel security standards. Georgia Crime Information Center (GCIC) staff work with eligible vendors to streamline the fingerprinting process per the requirements of the FBI’s CSP and the Rules of the Georgia Crime Information Center Council. Please note that the CJIS Vendor Compliance program does not certify that the vendor’s technical services, products or solutions are compliant with the FBI’s CSP nor does it confer any type of license or certification to the vendor for said services, products or solutions.
What are the personnel security requirements for vendor personnel who access CJI?
Policy Area 12 of the FBI’s CSP and GCIC Council Rules require all personnel with access to CJI in the State of Georgia to complete national fingerprint-based background checks, security awareness training and sign statements to confirm an understanding of CJI data and the laws mandating the protection of this data.
Why should a vendor take part in the program?
While participation in the program does not confer any special rights, license or privilege, it does save a vendor considerable time and resources. By centralizing some of the personnel security requirements the need to submit duplicate background checks for the same vendor personnel in cases where the vendor has multiple criminal justice customers is no longer necessary.
Prior to implementation vendor personnel with access to CJI had to submit a set of fingerprints for state and national fingerprint-based record checks for each agency with which they contract. This resulted in the need for vendors that support multiple clients to submit duplicate fingerprints in order to meet policy requirements. For example, if a given vendor had 50 employees and served 25 agencies then a total of 1250 fingerprints would need to be completed by the vendor with 50 results being kept by each of the vendor’s 25 agency customers.
Why can’t a vendor use participation in the program to market its services?
Vendors should not use participation in the program to market products or services because participation in the program does not indicate that the vendor is licensed or confirmed to be compliant with the CSP.
What is the local criminal justice agency’s role in the CJIS Vendor Compliance program?
Criminal justice agencies have a vital role in the program because agencies must first confirm that they have entered into a contract with a vendor before GCIC staff will begin to work with the vendor to complete personnel security requirements. Signed contracts between agencies and vendors must be related to the administration of criminal justice. When an agency contracts with a vendor, the vendor can take advantage of the centralized CJIS Vendor Compliance program and request that the agency work with GCIC to ensure vendor personnel undergo the necessary personnel security requirements.
To begin the process, agencies must send confirmation to GCIC that a contract exists between the vendor and the agency. The confirmation is submitted to the CJIS Vendor Compliance program by the agency (not vendor). Agencies that need more information about this process can contact their GCIC Customer Service representative or Compliance Specialist.
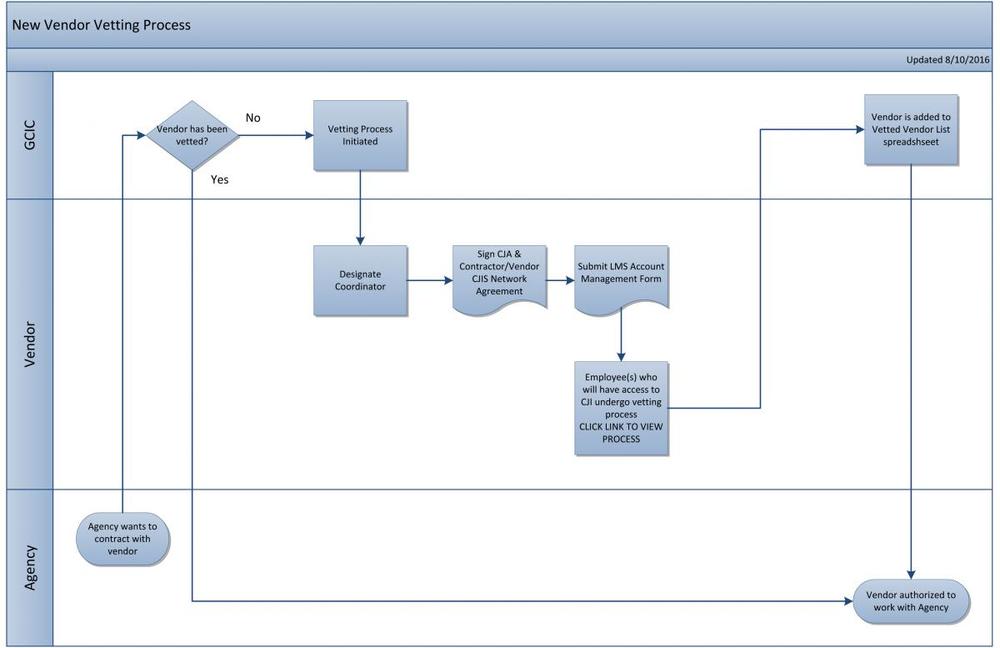
Vendor Personnel Compliance Process Overview
Before an agency contracts with a new vendor, it should check with GCIC to see if the vendor has been vetted. If so, the agency contacts the Vendor Coordinator to confirm that all vendor employees who will have access to CJI at the agency have been properly vetted. If any have not, it is the vendor’s responsibility to ensure that those employees are vetted prior to performing any work at the agency.
If the vendor has not been previously vetted by GBI, the vetting process is initiated and the following steps are taken:
- The vendor designates a Coordinator who will be the single point of contact for all matters related to vetting.
- The vendor downloads and signs the
CJA/G-NCJA and Vendor CJIS Network & Data Agreement .
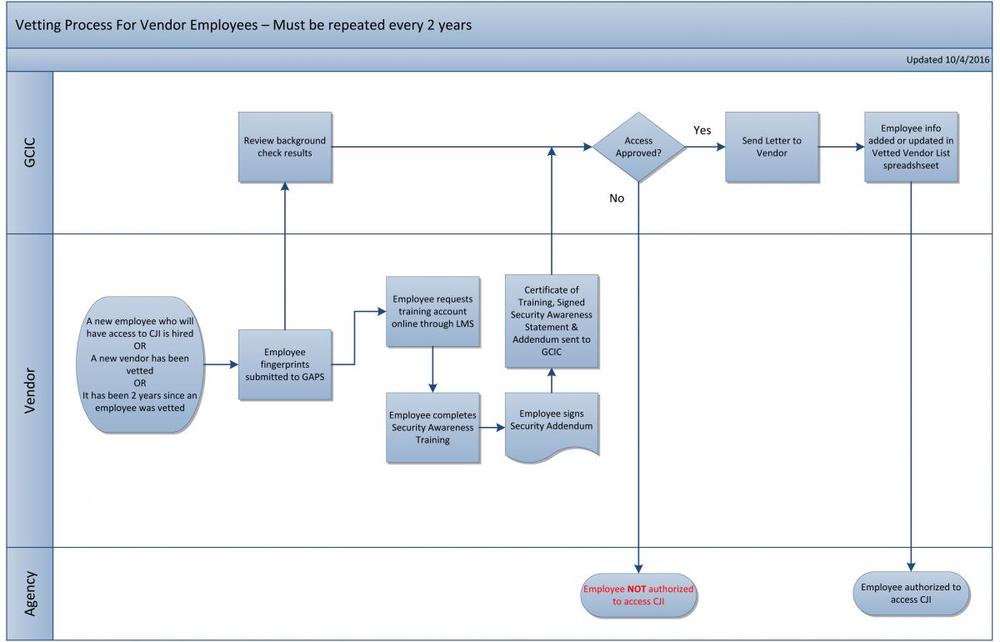
- Each employee who will have access to CJI must:
- Submit fingerprints to the Georgia Applicant Processing Service (GAPS) website for a national and state check.
- The employee will be notified by mail whether they have received approval to access CJI. Approved employees continue with the following steps:
- GBI vendor designated Coordinator requests a new training account from the GBI Vendor Contract Personnel.
- Once established, the employee logs into LMS, completes Security Awareness training and signs the Awareness Statement on-line. Note: Security Awareness training must be completed yearly.
- The employee signs the FBI Security Addendum. Note that a vendor representative must also sign this form.
- Note: fingerprint-based background checks must be completed every 2 years.
- Employees who are not approved will receive a letter including all information pertinent to that decision. The vendor will receive a letter simply stating that the employee has not been approved. For more information see Personnel Security Requirements.
- The Vendor Coordinator returns the signed Awareness Statement, FBI Security Addendum and Certificate of Training (available from the LMS system) to GCIC. Note: this step is also required every 2 years.
- The vendor and all approved employees are added to the Vetted Vendor List maintained by GCIC.
LMS LOGIN instructions for existing users:
Click here - LMS and enter the existing/previous username (without GBI_). Click 'Forgot Password' and complete the online boxes. The password reset link will be sent to the email address that’s on file.
The following diagrams offer a visual overview of the process (click to expand):

For more information, please contact GCIC at [email protected]